Service And Device Class of Bluetooth
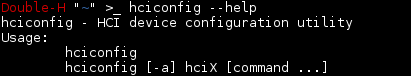
The following are some of the list of services and devices in the class that we can use to bluetooth exploitation. 1. List Bluetooth Class Device AUDIO_VIDEO (Value: 0x00000400) COMPUTER (Value: 0x00000100) HEALTH (Value: 0x00000900) IMAGING (Value: 0x00000600) MISC (Value: 0x00000000) NETWORKING (Value: 0x00000300) PERIPHERAL (Value: 0x00000500) PHONE (Value: 0x00000200) TOY (Value: 0x00000800) UNCATEGORIZED (Value: 0x00001f00) WEARABLE (Value: 0x00000700) 2. List Bluetooth Class Service AUDIO (Value: 0x00200000) CAPTURE (Value: 0x00080000) INFORMATION (Value: 0x00800000) LIMITED_DISCOVERABILITY (Value: 0x00002000) NETWORKING (Value: 0x00020000) OBJECT_TRANSFER (Value: 0x00100000) POSITIONING (Value: 0x00010000) RENDER (Value: 0x00040000) TELEPHONY (Value: 0x00400000) HOW TO..??? hciconfig = is used to configure Bluetooth devices. hci0 = the name of a Bluetooth device installed in the system. for help use this command: hciconfig --help ...