Nmap Vs Portsentry And Kill Port
Goodnight loyal readers art explo1t , this evening I returned to write a simple post but be bad if we leave it alone. before attackers exploit should first perform port scanning against their targets through the slit to know where they will infiltrate.
Equipment:
1. Nmap
2. Portsentry
3. Fuser
Here I use the Kali Linux operation system, so both the above equipments have been installed by default unless portsentry and we have to install it manually.
I did the following test:
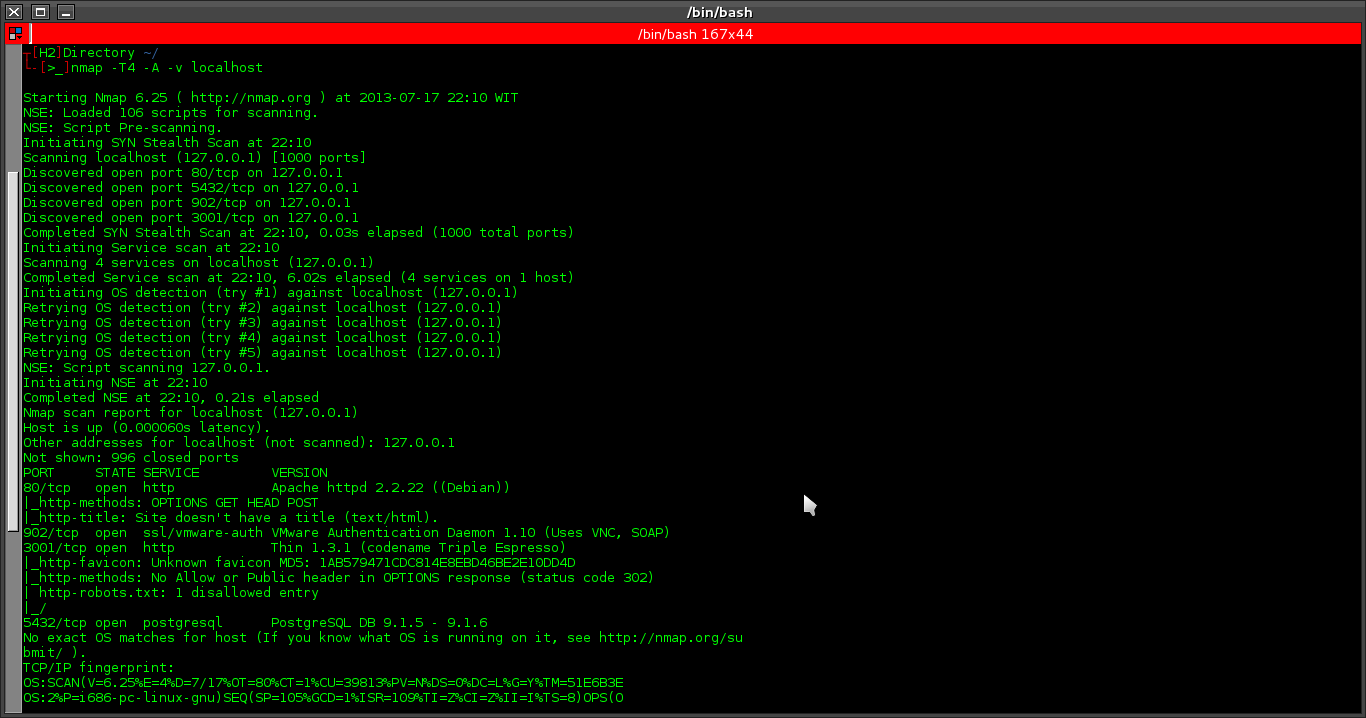
Seen in the picture above, nmap managed to find 4 open ports, and whether to enable portsentry can affect the workings of nmap. let's rock =))
Install Portsentry:
then edit portsentry.conf
Configuration blocking UDP / TCP scans to ignore options. search this section :
then replace with this:
blocking configuration with the host in order to block the connection Ipchain. subsequent search this section and uncheck #
Filtering configuration with TCP wrapper host. subsequent search this section and uncheck #
then save the settings above and starting a portsentry:
Seen in the picture above portsentry successfully manipulate the port scanning is done by Nmap
To Determine the activity of the portsentry data through syslog:
Further to close open ports ports can use the fuser:
seen on the picture above to ssh port 22 is open, then I will kill the port:
seen in the picture above that the port 22 for ssh has been closed
Regards Exploit:
Hidemichi-Hiroyuki a.k.a [H2]
Equipment:
1. Nmap
2. Portsentry
3. Fuser
Here I use the Kali Linux operation system, so both the above equipments have been installed by default unless portsentry and we have to install it manually.
I did the following test:
nmap -sV localhost
nmap -T4 -A -v localhost

Install Portsentry:
# apt-get install portsentry
then edit portsentry.conf
# nano /etc/portsentry/portsentry.conf
Configuration blocking UDP / TCP scans to ignore options. search this section :
BLOCK_UDP="0"
BLOCK_TCP="0"
BLOCK_TCP="0"
then replace with this:
BLOCK_UDP="1"
BLOCK_TCP="1"
The case serves to block TCP and UDP port scanning.BLOCK_TCP="1"
blocking configuration with the host in order to block the connection Ipchain. subsequent search this section and uncheck #
KILL_ROUTE="/sbin/iptables -I INPUT -s $TARGET$ -j DROP"
To reject clicking attacker host connections using iptables when caught doing scanning activitiesFiltering configuration with TCP wrapper host. subsequent search this section and uncheck #
KILL_HOSTS_DENY="ALL: $TARGET$ : DENY"
IP filter acces host attacker when caught doing port scanning on a network.then save the settings above and starting a portsentry:
# service portsentry start
or
# /etc/init.d/portsentry start
so, i then re-scan using nmap like the first step of the above:
# nmap -sV localhost
# nmap -T4 -A -v localhost
Seen in the picture above portsentry successfully manipulate the port scanning is done by Nmap
To Determine the activity of the portsentry data through syslog:
# tail -f /var/log/syslog
Further to close open ports ports can use the fuser:
# nmap -O localhost
seen on the picture above to ssh port 22 is open, then I will kill the port:
# fuser -k 22/tcp
options -k for kill port
after killing the port and then I look back on open ports:seen in the picture above that the port 22 for ssh has been closed
Regards Exploit:
Hidemichi-Hiroyuki a.k.a [H2]















Comments
Post a Comment
Do Not Fuckin Spamming