Forensic - Zbot Trojan Horse Analysis
Zeus or Zbot Trojan Horse is a computer malware running on the computer under the Microsoft Windows operating system version, this is done attacker to perform malicious tasks such as stealing banking information etc..
you can continue it here
Volatility
testing this time I have received a file that has been in infections by Zeus Trojan named "zeus.vmem"
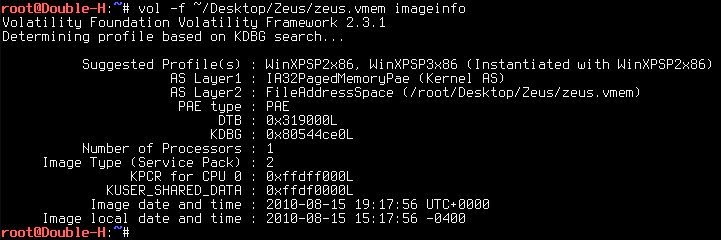
1.) The first stage uses the command "imageinfo" Identify information for the image.
-f = filename
imageinfo = Identify information for the image
next, we can use the command "pslist" to display a list of the overall process on the file "zeus.vmem"
command:
seen in the picture above we have not found something strange, then we can try to call the command "connscan" to see if the file make a connection
command:
The file looks to make a connection with the address "193.104.47.75" on port 80 as well as using PID "856"
next, we use the command "pstree" to print a list of the listening process.
command:
seen in the section there are colored, I will explain in the next step :)
next Print list of registry hives using options "hivelist"
command:
HKEY Current User ( HKCU ) lies hidden in the NTUSER.DAT file from the directory \Documment and Settings\. there are some other, more important branches are HKEY Local Machine ( HKLM ) and branches to software located in the directory \Windows\system32\config\ . (see the section I marked above.)
next, Print a registry key, and its subkeys and values with options "printkey"
command:
UserInit is a program that determines what should be run after the user logs into Windows. The default program is located in the C:\windows\system32\userinit.exe. userinit.exe a program that returns the user's profile, fonts, colors and others. in that section It is a common place for trojans.
now, find hidden and injected code with options "malfind"
command:
--dump-dir ~/Desktop/Zeus/ = output will be stored in the directory ~/Desktop/Zeus/
in the section above on "pstree" there are some parts that I gave the paint.
we can see which Winlogon.exe run sdra64.exe and svchost.exe (PID 856) mengubungkan to the internet and service.exe (PPID 676) has some code injection in it.
then we look for the SHA256 of process dump "process.0x80ff88d8.0xb70000.dmp" malfind results and see if the process is detected by VirusTotal
command:
you can see the results from Virus Total scanning here
Download Zbot
I think that's all my explanation today :)
Regards
Hidemichi-Hiroyuki a.k.a [H2]
you can continue it here
Volatility
testing this time I have received a file that has been in infections by Zeus Trojan named "zeus.vmem"
1.) The first stage uses the command "imageinfo" Identify information for the image.
root@Double-H:~# vol -f ~/Desktop/Zeus/zeus.vmem imageinfo
-f = filename
imageinfo = Identify information for the image
next, we can use the command "pslist" to display a list of the overall process on the file "zeus.vmem"
command:
root@Double-H:~# vol -f ~/Desktop/Zeus/zeus.vmem pslist
seen in the picture above we have not found something strange, then we can try to call the command "connscan" to see if the file make a connection
command:
root@Double-H:~# vol -f ~/Desktop/Zeus/zeus.vmem connscan
The file looks to make a connection with the address "193.104.47.75" on port 80 as well as using PID "856"
next, we use the command "pstree" to print a list of the listening process.
command:
root@Double-H:~# vol -f ~/Desktop/Zeus/zeus.vmem pstree
seen in the section there are colored, I will explain in the next step :)
next Print list of registry hives using options "hivelist"
command:
root@Double-H:~# vol -f ~/Desktop/Zeus/zeus.vmem hivelist
HKEY Current User ( HKCU ) lies hidden in the NTUSER.DAT file from the directory \Documment and Settings\. there are some other, more important branches are HKEY Local Machine ( HKLM ) and branches to software located in the directory \Windows\system32\config\ . (see the section I marked above.)
next, Print a registry key, and its subkeys and values with options "printkey"
command:
root@Double-H:~# vol -f ~/Desktop/Zeus/zeus.vmem printkey -K "Microsoft\Windows NT\CurrentVersion\Winlogon"
UserInit is a program that determines what should be run after the user logs into Windows. The default program is located in the C:\windows\system32\userinit.exe. userinit.exe a program that returns the user's profile, fonts, colors and others. in that section It is a common place for trojans.
now, find hidden and injected code with options "malfind"
command:
root@Double-H:~# vol -f ~/Desktop/Zeus/zeus.vmem malfind --dump-dir ~/Desktop/Zeus/
--dump-dir ~/Desktop/Zeus/ = output will be stored in the directory ~/Desktop/Zeus/
in the section above on "pstree" there are some parts that I gave the paint.
we can see which Winlogon.exe run sdra64.exe and svchost.exe (PID 856) mengubungkan to the internet and service.exe (PPID 676) has some code injection in it.
then we look for the SHA256 of process dump "process.0x80ff88d8.0xb70000.dmp" malfind results and see if the process is detected by VirusTotal
command:
root@Double-H:~# sha256sum ~/Desktop/Zeus/process.0x80ff88d8.0xb70000.dmp
you can see the results from Virus Total scanning here
Download Zbot
I think that's all my explanation today :)
Regards
Hidemichi-Hiroyuki a.k.a [H2]













keren ^_^
ReplyDelete=))
ReplyDeleteThanks bro
ReplyDelete